The Most Comprehensive Cloud Endpoint Protection
Provides advanced security for all your endpoints, which are the Launchpad of malware attacks.
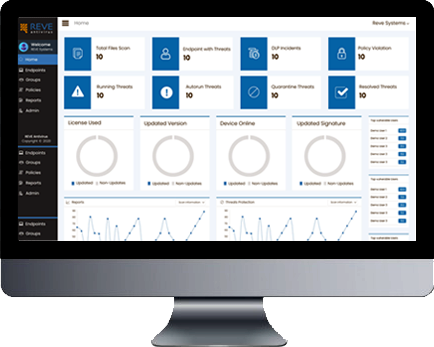
Helps manage all your Endpoints from a single management cloud console.
Facilitates remote installation, updating, and scanning of all individual end point PCs.
Machine learning technology that strengthens defense against targeted attacks & zero day virus.
Centralized Management Console
Client management from a single centralized dashboard withsecure access. REVE Endpoint Security Solution provides asimple and user-friendly console to manage entire endpoint network from the cloud from any location.
Device Control
The devices within organisation remains under control of End Point Cloud admin ensuring there is no theft or mishandling of confidential data. Various types of storage devices like Pen Drive, Card Reader, CD/DVD ROM etc., can be restricted by admin remotely.
Application Control
Configuring app usage restrictions on End Point Cloud Clients, Admin can apply control on installed applications.
Asset Management
Asset information (OS, Processor, Memory, Storage etc.) for every deployed client can be directly fetched from a central console.
Firewall
A host-based firewall with configurable rules allows admin to filter inbound or outbound traffic. It also provides option to create rules based on different protocol type’s viz., TCP, UDP or ICMP.
IPS/IDS
REVE EndPoint Cloud is detects 5 attacks along with Automatic Prevention:
- DDOS Attack
- ICMP Attack
- RDP Attack
- SMB Attack
- Syn-Floyd Attack
Anti- Ransomware
Anti-Ransomware feature will protect your important folder from being attacked by Ransomware. Once you add a folder/path, Ransomware protection will protect that path from any violations, if any process trying to write or encrypt that folder REVE will block automatically. REVE Client Has an option to unblock a process from client UI.
Data Loss Prevention (DLP)
REVE End Point Cloud offers a dynamic enterprise feature through which various data transfer channels like Removable Devices, Local Network Sharing, Online File Transfer, Print Screen etc., can be restricted for data transfer. This helps to maintain the high level of confidentiality, meeting the data security standards for any organization.
Extensive Reports
End Point Cloud generates reports for various events of all the connected endpoints helps to scrutinize and trace the policy breaches by users.
- AntiMalware/Antiransomware reports
- Web reports for Unauthorized access/Antiphishing
- Unauthorized Device access reports
- Unauthorized Application access reports
- Unauthorized Uninstall reports
- Data Loss Prevention reports
Device Control
The devices within organisation remains under control of End Point Cloud admin ensuring there is no theft or mishandling of confidential data. Various types of storage devices like Pen Drive, Card Reader, CD/DVD ROM etc., can be restricted by admin remotely.
REVE Endpoint Cloud
Features
Download Now


REVE Endpoint Cloud
Brochure
Download Now

Contact us for Free Assisted Demo

 United States
United States  Cloud
Cloud